Your own domain name mycompany.be is the basis of your online corporate identity: you can easily link your website and email addresses to it, as well as other online services. But the words online, identity and easily in one sentence also attract the interest of cybercriminals. For phishing, requesting ransomware or otherwise abusing this technology. There is no doubt that they will try. That is why you can read how to protect your domain with cybersecurity and what you should do here.
Your own domain name = greater visibility
Most companies have their own domain such as mycompany.com or a be/nl/co.uk… or a variant thereof. Occasionally you will see smaller SMEs using an email address with their provider’s domain such as mycompany@telenet.be. However, registering your own domain and turning it into a personalised email address is not that expensive and quite easy to do, so why wouldn’t you do it? It gives your company extra visibility. But the more email addresses and other applications depend on your domain name, the greater the risk of abuse…
Phishing risks: falsified invoices and payment orders
For example, the abuse of a fake email address with corresponding domain to send phishing mails is very popular. In that case, cybercriminals use domains that are very similar to yours, such as mycompany.com, my8company.com or mycompany.xxx.com. They mislead your employees, customers and suppliers. If you have your own clear domain name, point it out to your contacts. And also make them aware of the risks they are facing if they do respond to an email similar to yours without checking. An alert recipient can easily see that the sender is not a match for the actual domain name. It gets a lot harder when online criminals effectively use your domain. This is much less immediately visible. The abuse of your real domain name is a successful technique for sending fake invoices or payment orders in your name, for example. These are just some of the types of fraud that cybercriminals can commit if they have access to your domain name.
Cybersecurity to the rescue
Fortunately, there is security technology to help you combat such practices. SSL and SPF-DKIM-DMARC are the most accessible and efficient of their kind.
Protecting emails with SPF-DKIM-DMARC
This standard protects against the abuse by cybercriminals of email addresses with your domain name, but also against the sending of spam messages in your name.
The four major advantages of this standard are
-
Security – Your domain is no longer as attractive for use in phishing attacks which are usually followed by fraud or ransomware..
-
Visibility – All email usage of your domain is visible: all that is legitimate but also everything that could be fraudulent. This way you maintain control.
-
Delivery – Your domain will have a better reputation over time. This ensures the delivery of your emails and they won’t be blocked by firewalls or spam systems (any more). Marketing emails – advertising – are also passed on more easily.
-
Identity – You show up with a unique digital signature in your email header showing clearly you are the right sender.
A paying SSL certificate for your website
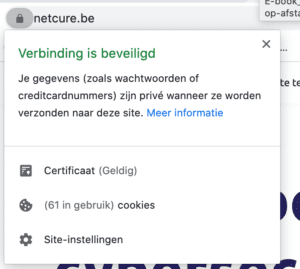
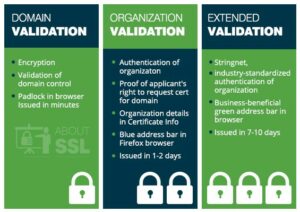
To prove online that your website is really yours, the use of an SSL certificate is a good thing. This certificate has two purposes:
-
Encrypting the connection between the visitor and your website.
he data traffic between the two is encrypted and thus unreadable for third parties.
-
Proof of identity.
Any website address marked with a lock and ‘https‘ is a correct address – not a fake lookalike.
Read more about how exactly you can recognise SSL from in this blog: Staying secure online while browsing
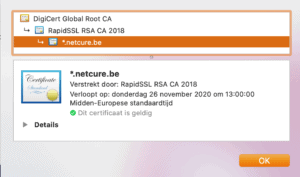
On websites, we often see free SSL certificates with a limited validity period which have to be renewed every time. This is fine for the first application, namely the secure connection between visitor and website.
HOWEVER: you have to be aware that this free certificate is also free for cybercriminals. They too make grateful use of https and SSL. This way they can activate a free certificate on a fake domain that is very similar to yours and the unsuspecting visitor thinks it is OK because the link starts with https://.
So, if you want to be sure, always use a paying certificate on your website or online services. Although it is not really expensive and it does appear to be a deterrent for people who want to abuse your good name. A paid certificate is valid for at least 12 months and clearly shows the name of your company. If in doubt, just check.
Would you like to find out how sensitive your company is to these practices? Contact us for a free check-up and advice.
Try us: this check-up and the accompanying advice are free of charge.